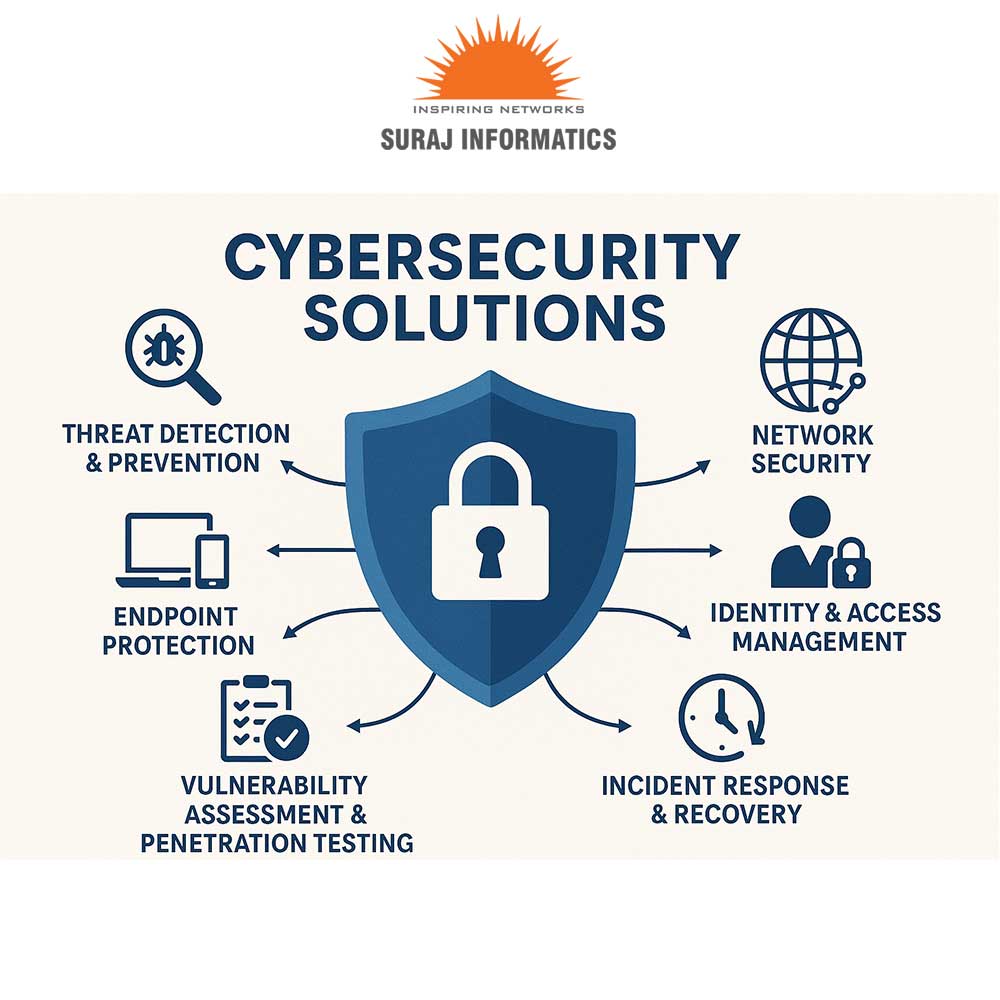
🔐 4. Identity & Access Management (IAM):
Control who gets access to what. We implement strong authentication, biometrics, role-based access control, and more to keep your data in the right hands. 🧑💼🔑
🧪 5. Vulnerability Assessment & Penetration Testing:
We simulate real-world attacks to uncover security gaps before hackers do. Then, we help patch them up quickly and efficiently. 🧑💻🔍
⚠️ 6. Incident Response & Recovery:
In case of a breach, our response team acts swiftly to contain the damage, recover lost data, and strengthen future resilience. ⏳🛠️
📝 7. Compliance & Risk Management:
Stay ahead of regulations like GDPR, ISO 27001, and more. We guide your business toward full compliance and minimal risk exposure. 📋✅