Cybersecurity Solutions by Suraj Informatics: Defend. Detect. Defeat
𝐈𝐧 𝐭𝐨𝐝𝐚𝐲’𝐬 𝐝𝐢𝐠𝐢𝐭𝐚𝐥-𝐟𝐢𝐫𝐬𝐭 𝐰𝐨𝐫𝐥𝐝, 𝐜𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐢𝐬 𝐧𝐨𝐭 𝐚 𝐜𝐡𝐨𝐢𝐜𝐞—𝐢𝐭’𝐬 𝐚 𝐧𝐞𝐜𝐞𝐬𝐬𝐢𝐭𝐲. 𝐀𝐬 𝐭𝐡𝐫𝐞𝐚𝐭𝐬 𝐞𝐯𝐨𝐥𝐯𝐞 𝐚𝐧𝐝 𝐡𝐚𝐜𝐤𝐞𝐫𝐬 𝐛𝐞𝐜𝐨𝐦𝐞 𝐦𝐨𝐫𝐞 𝐬𝐨𝐩𝐡𝐢𝐬𝐭𝐢𝐜𝐚𝐭𝐞𝐝, 𝐞𝐯𝐞𝐫𝐲 𝐛𝐮𝐬𝐢𝐧𝐞𝐬𝐬 𝐧𝐞𝐞𝐝𝐬 𝐚 𝐫𝐞𝐥𝐢𝐚𝐛𝐥𝐞 𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐩𝐚𝐫𝐭𝐧𝐞𝐫. 𝐓𝐡𝐚𝐭’𝐬 𝐰𝐡𝐞𝐫𝐞 𝐒𝐮𝐫𝐚𝐣 𝐈𝐧𝐟𝐨𝐫𝐦𝐚𝐭𝐢𝐜𝐬 𝐬𝐭𝐞𝐩𝐬 𝐢𝐧 𝐰𝐢𝐭𝐡 𝐧𝐞𝐱𝐭-𝐠𝐞𝐧𝐞𝐫𝐚𝐭𝐢𝐨𝐧 𝐜𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐬𝐨𝐥𝐮𝐭𝐢𝐨𝐧𝐬 𝐭𝐚𝐢𝐥𝐨𝐫𝐞𝐝 𝐭𝐨 𝐩𝐫𝐨𝐭𝐞𝐜𝐭 𝐲𝐨𝐮𝐫 𝐝𝐚𝐭𝐚, 𝐬𝐲𝐬𝐭𝐞𝐦𝐬, 𝐚𝐧𝐝 𝐫𝐞𝐩𝐮𝐭𝐚𝐭𝐢𝐨𝐧. 💻🛡️
𝐀𝐭 𝐒𝐮𝐫𝐚𝐣 𝐈𝐧𝐟𝐨𝐫𝐦𝐚𝐭𝐢𝐜𝐬, 𝐰𝐞 𝐩𝐫𝐨𝐯𝐢𝐝𝐞 𝐞𝐧𝐝-𝐭𝐨-𝐞𝐧𝐝 𝐜𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐬𝐞𝐫𝐯𝐢𝐜𝐞𝐬 𝐭𝐡𝐚𝐭 𝐬𝐚𝐟𝐞𝐠𝐮𝐚𝐫𝐝 𝐲𝐨𝐮𝐫 𝐨𝐫𝐠𝐚𝐧𝐢𝐳𝐚𝐭𝐢𝐨𝐧 𝐟𝐫𝐨𝐦 𝐩𝐨𝐭𝐞𝐧𝐭𝐢𝐚𝐥 𝐜𝐲𝐛𝐞𝐫𝐚𝐭𝐭𝐚𝐜𝐤𝐬, 𝐝𝐚𝐭𝐚 𝐛𝐫𝐞𝐚𝐜𝐡𝐞𝐬, 𝐦𝐚𝐥𝐰𝐚𝐫𝐞, 𝐫𝐚𝐧𝐬𝐨𝐦𝐰𝐚𝐫𝐞, 𝐩𝐡𝐢𝐬𝐡𝐢𝐧𝐠, 𝐚𝐧𝐝 𝐢𝐧𝐬𝐢𝐝𝐞𝐫 𝐭𝐡𝐫𝐞𝐚𝐭𝐬. 𝐖𝐡𝐞𝐭𝐡𝐞𝐫 𝐲𝐨𝐮’𝐫𝐞 𝐚 𝐬𝐭𝐚𝐫𝐭𝐮𝐩, 𝐞𝐧𝐭𝐞𝐫𝐩𝐫𝐢𝐬𝐞, 𝐨𝐫 𝐠𝐨𝐯𝐞𝐫𝐧𝐦𝐞𝐧𝐭 𝐚𝐠𝐞𝐧𝐜𝐲, 𝐰𝐞 𝐞𝐧𝐬𝐮𝐫𝐞 𝐲𝐨𝐮𝐫 𝐝𝐢𝐠𝐢𝐭𝐚𝐥 𝐚𝐬𝐬𝐞𝐭𝐬 𝐚𝐫𝐞 𝐟𝐨𝐫𝐭𝐢𝐟𝐢𝐞𝐝 𝐰𝐢𝐭𝐡 𝐢𝐧𝐭𝐞𝐥𝐥𝐢𝐠𝐞𝐧𝐭, 𝐬𝐜𝐚𝐥𝐚𝐛𝐥𝐞, 𝐚𝐧𝐝 𝐜𝐨𝐬𝐭-𝐞𝐟𝐟𝐞𝐜𝐭𝐢𝐯𝐞 𝐝𝐞𝐟𝐞𝐧𝐬𝐞𝐬. 🧠💼
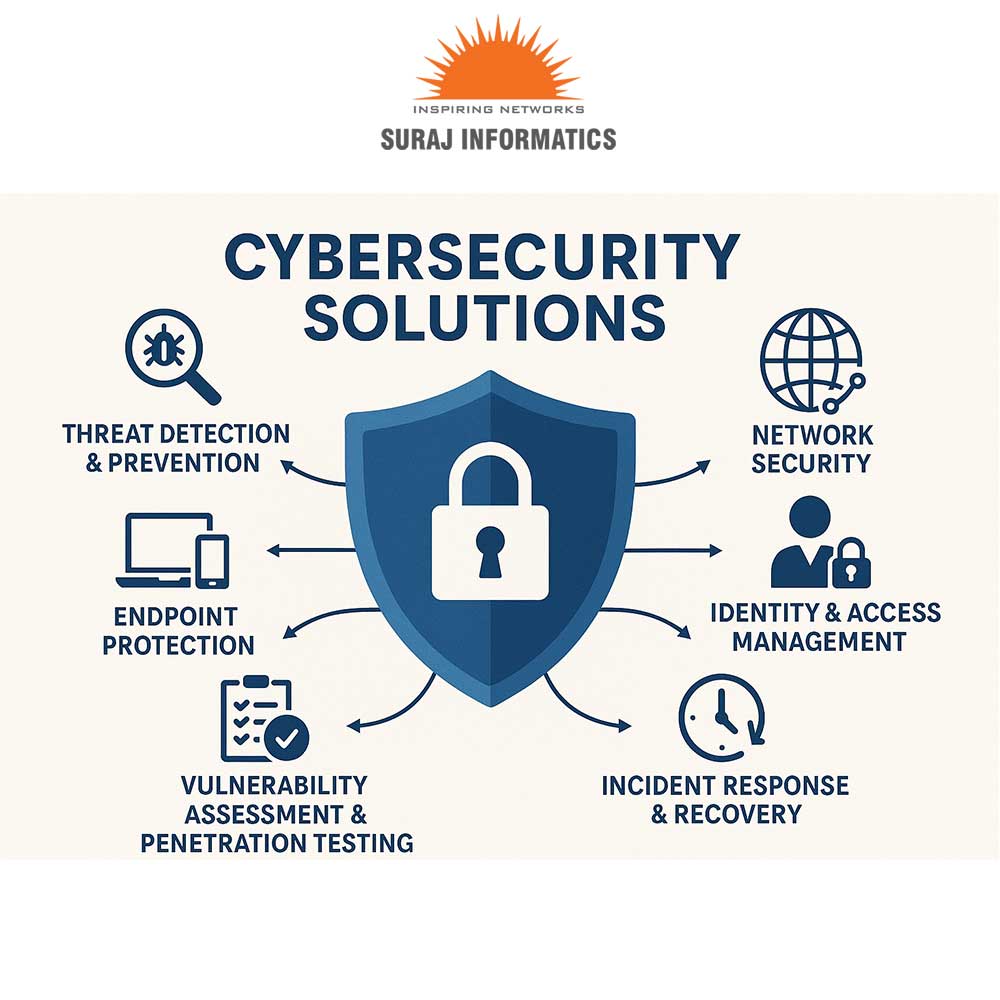
🔐 4. Identity & Access Management (IAM):
Control who gets access to what. We implement strong authentication, biometrics, role-based access control, and more to keep your data in the right hands. 🧑💼🔑
🧪 5. Vulnerability Assessment & Penetration Testing:
We simulate real-world attacks to uncover security gaps before hackers do. Then, we help patch them up quickly and efficiently. 🧑💻🔍
⚠️ 6. Incident Response & Recovery:
In case of a breach, our response team acts swiftly to contain the damage, recover lost data, and strengthen future resilience. ⏳🛠️
📝 7. Compliance & Risk Management:
Stay ahead of regulations like GDPR, ISO 27001, and more. We guide your business toward full compliance and minimal risk exposure. 📋✅
🌍 Why Choose Suraj Informatics?
🤖 Proven expertise in IT Security & Automation
🚛 Customized solutions for ports, logistics, government, and enterprises
🏪 24×7 support with dedicated response teams
🚃Cost-effective and scalable deployment
🌎 Trusted by leading businesses across the globe
𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐢𝐬𝐧’𝐭 𝐣𝐮𝐬𝐭 𝐚𝐛𝐨𝐮𝐭 𝐝𝐞𝐟𝐞𝐧𝐝𝐢𝐧𝐠 𝐚𝐠𝐚𝐢𝐧𝐬𝐭 𝐭𝐡𝐫𝐞𝐚𝐭𝐬—𝐢𝐭’𝐬 𝐚𝐛𝐨𝐮𝐭 𝐛𝐮𝐢𝐥𝐝𝐢𝐧𝐠 𝐭𝐫𝐮𝐬𝐭 𝐰𝐢𝐭𝐡 𝐲𝐨𝐮𝐫 𝐜𝐥𝐢𝐞𝐧𝐭𝐬, 𝐩𝐚𝐫𝐭𝐧𝐞𝐫𝐬, 𝐚𝐧𝐝 𝐞𝐦𝐩𝐥𝐨𝐲𝐞𝐞𝐬. 💼🔒 𝐒𝐮𝐫𝐚𝐣 𝐈𝐧𝐟𝐨𝐫𝐦𝐚𝐭𝐢𝐜𝐬 𝐞𝐦𝐩𝐨𝐰𝐞𝐫𝐬 𝐲𝐨𝐮 𝐭𝐨 𝐨𝐩𝐞𝐫𝐚𝐭𝐞 𝐰𝐢𝐭𝐡 𝐜𝐨𝐧𝐟𝐢𝐝𝐞𝐧𝐜𝐞 𝐢𝐧 𝐚 𝐜𝐨𝐧𝐧𝐞𝐜𝐭𝐞𝐝 𝐰𝐨𝐫𝐥𝐝.
🌟 𝐒𝐞𝐜𝐮𝐫𝐞 𝐲𝐨𝐮𝐫 𝐝𝐢𝐠𝐢𝐭𝐚𝐥 𝐟𝐮𝐭𝐮𝐫𝐞 𝐰𝐢𝐭𝐡 𝐒𝐮𝐫𝐚𝐣 𝐈𝐧𝐟𝐨𝐫𝐦𝐚𝐭𝐢𝐜𝐬.
𝐋𝐞𝐭’𝐬 𝐛𝐮𝐢𝐥𝐝 𝐚 𝐜𝐲𝐛𝐞𝐫-𝐫𝐞𝐬𝐢𝐥𝐢𝐞𝐧𝐭 𝐛𝐮𝐬𝐢𝐧𝐞𝐬𝐬 𝐭𝐨𝐠𝐞𝐭𝐡𝐞𝐫! 🔐🤝
📍 𝐂𝐨𝐧𝐭𝐚𝐜𝐭 𝐔𝐬 𝐓𝐨𝐝𝐚𝐲!
📧 𝐬𝐚𝐥𝐞𝐬@𝐬𝐮𝐫𝐚𝐣𝐢𝐧𝐟𝐨𝐫𝐦𝐚𝐭𝐢𝐜𝐬.𝐜𝐨𝐦
📞 +𝟗𝟏-𝟐𝟐-𝟒𝟎𝟑𝟎𝟗𝟖𝟎𝟎
🏢 𝐄 𝟐𝟎𝟑, 𝐓𝐨𝐰𝐞𝐫 𝐍𝐨 𝟕, 𝐂𝐁𝐃 𝐁𝐞𝐥𝐚𝐩𝐮𝐫, 𝐍𝐚𝐯𝐢 𝐌𝐮𝐦𝐛𝐚𝐢 – 𝟒𝟎𝟎𝟔𝟏𝟒 | 🌐 www.surajinformatics.com
